Here is an article discussing a new security measure for cell phones. The legislation is currently (Feb 2014) under discussion in California. (Basically, a law requiring a way to disable a stolen phone.)
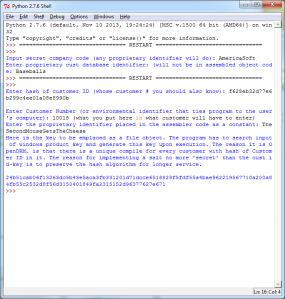
Security and secrecy interact, and secrecy in escrow appears to be a theoretical problem in security. Passwords are secret and rightfully should be, but just as a bank vault cannot be made secure for infinite time, so we must theorize some procedure to account for a compromised escrow system. Bank vaults are secure either because it costs more to break into them than the contents are worth, or because they are monitored at intervals, such that the time required to break in, exceeds the interval, and the attacker would become observed.
If the Corporation is the escrow system, questions that make us think about how some attacker might hijack the system help us think about how an attacker would misuse it.
When we legislate about security, we take a step that is hard to modify later. This makes legislating difficult, because, as George Polya noted, our early efforts at solutions are not usually perfect solutions. A reasonable step to mitigate this problem might be to implement the concept of a pilot program, while this is not a panacea.
Security and secrecy are intertwined concepts, and when we legislate about security it is important to subject the provisions for secrecy to the scrutiny of rational skepticism.
Kirchhoff’s Principle is an example of this, and it is often unpopular. People are skeptical of an argument that first advances the premise that secrecy is only possible for finite time, and then advises end users to be satisfied that the entire security of the system ride solely on the secrecy of the password.
The reason that this is good, is that it reduces the discussion to a single point of failure. A person can reasonably be held responsible for the secrecy of a password, where s/he could not be held responsible for the secrecy of an entire system. We, as humans, also intuitively understand how to keep a password secret, and when it is compromised.
In this example, we can usefully ask these questions:
- Is it necessary? In a State of the Union address, President Obama required two things for an infrastructure bank. 1. The loans must be for infrastructure. and 2. The infrastructure must be needed. In the news article, the expedience of the new law is argued from the observation that cell phone theft represents a large fraction of a particular crime statistic.
- Will the measure be drastic, or a mere deterrent? Apple’s solution of requiring login credentials on demand, adequately discourages theft. For purposes of illustration we could alternatively choose a permanent “bricking” measure for the cell phone program we are talking about. Such an extreme measure makes the implementor give careful consideration to the accountability procedures of those authorized to “pull the trigger.”
- How will the public be protected from governmental abuse? For example, what if irresponsible campaign staffers took to the practice of bricking each other’s phones during a campaign? What would protect them from each other, or protect innocent [third] parties from a kind of political “hit and run?” Here, we see that the private corporation is responsible, not the police department, as has been suggested for car “kill switches.” Presumably an irresponsible corporation can be sued or fined.
- Does it preserve individual freedom? In the case of a car, we should to be able to drive it even when this is unauthorized. For example, driving an injured person to the hospital, even if the driver were unlicensed, or had failed to make his car insurance payment. This question is a way to account for possible civil rights abuses. In the case of a cell phone, can you call 911? At the moment we can’t do that anyway; we might want emergency help, but we do not want to be tracked by a homing beacon.
- Does it solve the problem even if we do not like it? This measure deals definitively with the use of a stolen device, without actually locating the thief. Good to stop online gambling at a consumer’s expense; bad for eventual arrest and ultimate prosecution of the thief. It is politically pragmatic to discourage crime, even if there is no criminal prosecution.
- Might this measure open the door to some form of regulatory capture? For example. would a customer who was trying to get his phone reactivated face prejudice as to whether or not he was creating a nuisance, because of various other possible infractions?
A very American way of introducing the above-cited discussion, would be for the manufacturer to implement some program, and then wait for someone to challenge the legality of the behavior in a court of law. This might describe the course that Gen. Alexander’s NSA has recently taken.
When a corporation does this, it leaves the outcome subject to a less researched political environment than if it is debated in a legislature. It has the advantages of allowing for improvement (as Polya’s method suggests,) and preserving the freedom and autonomy of corporations. The reason that the NSA is currently unpopular, is that it undertook an extensive initiative without publishing, resulting in the appearance of a secret agenda. The NSA is governmental, not a civilian enterprise.
Good law is maintained when the legislation is carefully devised, and worded so that it is hard to misinterpret or abuse.
Both strategies are deliberated, one by the legislature, the other by the courts. In America we want to preserve freedom, despite the din of mediocrity.